Encrypted Workstation FAQ
Overview
Data encryption is an important tool in our information security toolbox. Learn more through the answers to common questions below.
Frequently Asked Questions
Can I use alternative encryption technologies to meet the encryption requirement for RESTRICTED information storage?
Although many products provide valid encryption, many are not very usable in an enterprise setting. Our current standard for desktop encryption provides these important usability features:
- Centrally managed, logged, and audited ability to unlock a machine when a passphrase is forgotten or when it is lost due to employee separation.
- Central reporting of what machines are encrypted.
- Central logging of errors and login failures.
The University's information classification and protection policy mandates that approved encryption technology be used to control restricted data stored on computers. Schedule C referenced in that policy provides a list of currently approved encryption technologies.
I don't think there's encrypted information stored on my (or my staff) computers. Should I encrypt just to be safe?
Are you sure there is no restricted data? You may want to run SENF and check for SSN, CCN on the drive(s). If you're sure you have no restricted information stored temporarily, occasionally, or regularly on the system, then, generally speaking, you should not encrypt. Why? Encryption comes at a cost. Aside from the cost of the software and backup drive, there is technician time in setup and extra maintenance when you transfer the machine or when people come and go from your department (e.g., if a person is an alternate user on several machines and is separated, you have to remove their login from the disks in order to preserve our protection).
Why is our encryption not compatible with the latest hardware or software?
Often it is, but encryption users cannot expect to be leading adopters of new hardware and operating systems. In order to make an encrypted workstation transparent to use, the encryption is tightly integrated to the hardware and operating system. Big changes in operating systems and hardware may change the way that integration works, and the encryption vendors have to catch up. This means that encrypted workstation users should not expect to be early adopters of the latest hardware and operating systems; they should expect to be six months behind the cutting edge.
Can I update my encrypted computer?
Normal software updates and patches are still an encouraged part of best practices and standard usage of any computer system. Upgrades must wait until WDE supports the upgrade — otherwise, you may destroy your data. Let's review the definitions and differences between an "upgrade" and an "update."
-
Upgrade: A major change to a software or operating system product. Such products are often something you purchase. MacOS upgrades are sometimes also called "reference releases." Example: macOS 10.15 (Catalina) is an upgrade from macOS 10.14 (Mojave). Windows 11 is an upgrade for Windows 10.
-
Update: A version change within the same software release, but it does not upgrade it to the next major version (if one exists). Software updates often include bug fixes and security updates for existing software. Software updates are made available via automated update or download from the software vendor, often through included system update utilities. Mac and Windows systems both have processes that download and apply software updates to the base system. Example: macOS 23.3 is an update from macOS 23.2 or earlier.
Encryption Software Updates
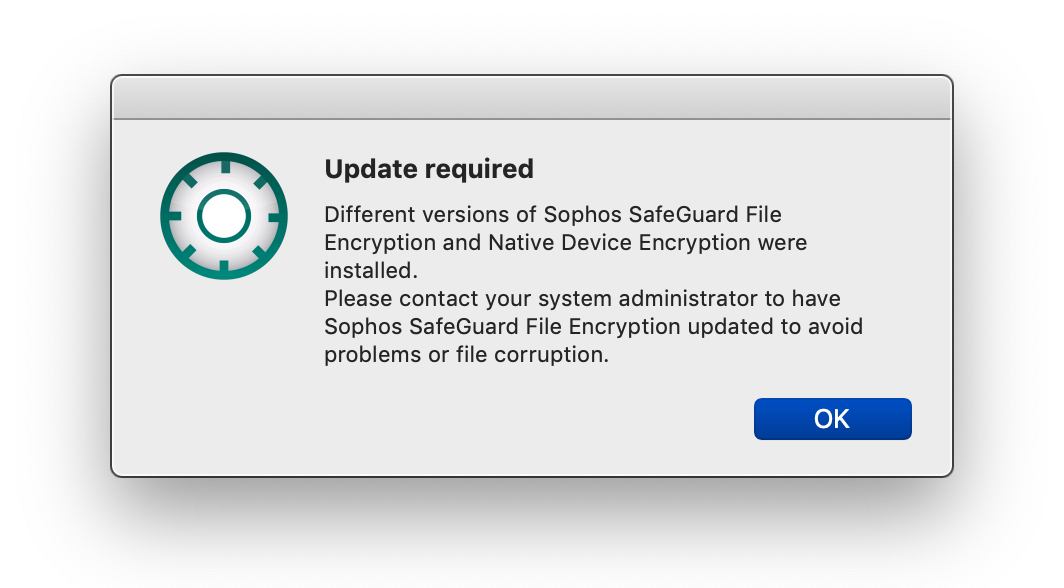
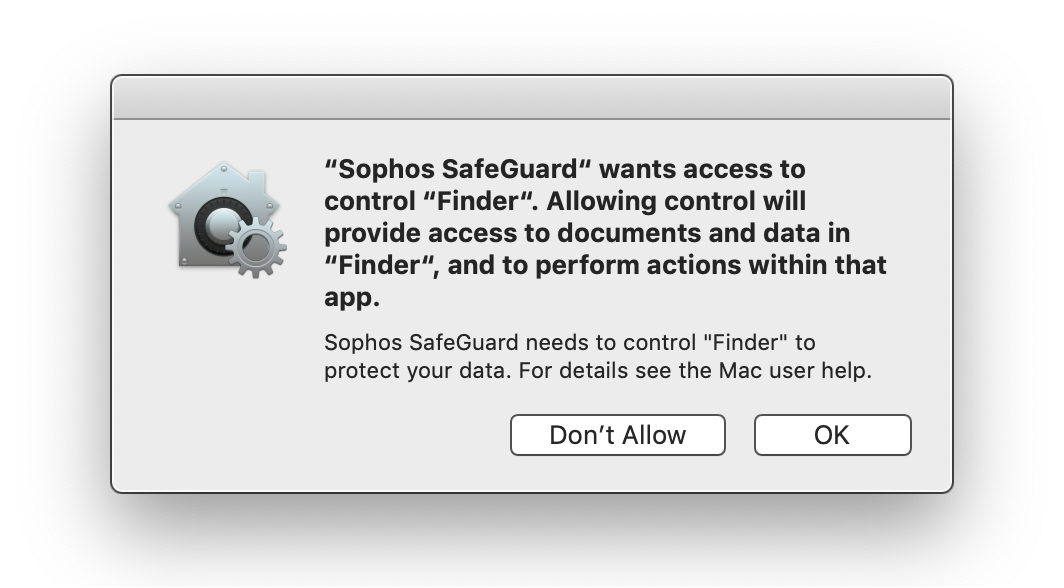
Updates to the installed software that manages device encryption often need to be applied when new operating system upgrades are released. Beginning with macOS 10.14 (Mojave), Apple added additional security controls that alert users to important changes to software or permissions when it is installed or updated. Encrypted Mac computers may display the following pop-up windows during installs and upgrades. You must accept the changes by clicking OK, or encryption may malfunction.
 |
 |
|
Click OK. This is a temporary version mismatch that is resolved by the completion of the update in progress. No additional actions are required. |
Click OK. Failure to provide SafeGuard access to Finder may cause your encryption to malfunction. |
← Back to Encrypted Workstation Home